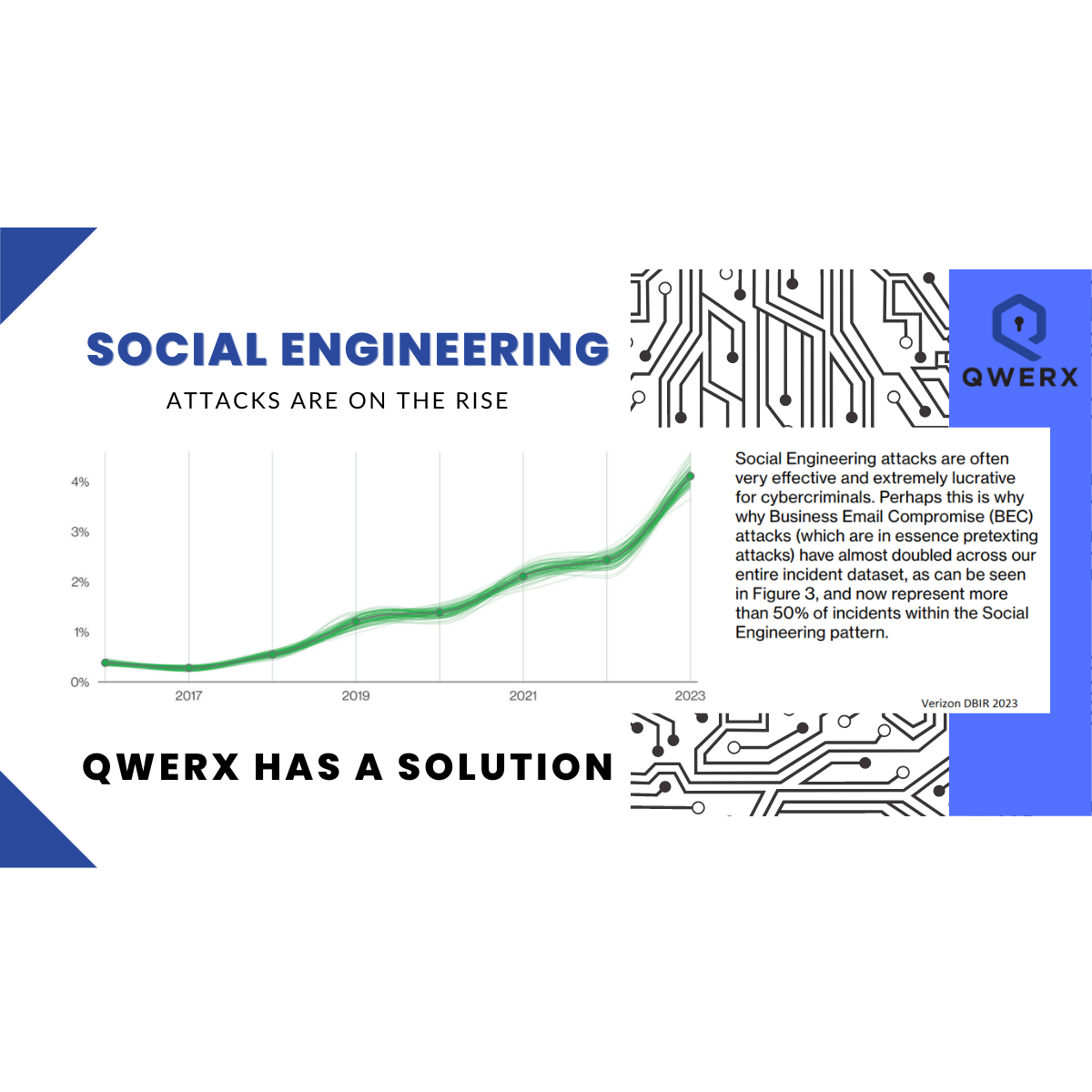
A New Way to Prevent Credential Harvesting
In today's digital age, where nearly every aspect of our lives is online, the security of personal and sensitive information has become paramount. One significant threat that continues to loom over the cybersecurity landscape is credential harvesting. Hackers and cybercriminals employ various techniques to acquire usernames, passwords, and other authentication details, putting individuals and organizations at risk. In the battle against this ever-evolving menace, QWERX's dynamic machine authentication solution emerges as a powerful and innovative defense mechanism.
Understanding Credential Harvesting
Credential harvesting, also known as credential theft, involves the unauthorized acquisition of login credentials. There are many solutions on the market that aim to secure user credentials like passwords. At QWERX, we are most concerned with the vulnerability of static SSH certificates that authorize a device to access a network. Once attackers gain access to these credentials, they can compromise accounts, steal sensitive data, and wreak havoc on both individuals and organizations.
The Threat Landscape
The prevalence of credential harvesting poses a significant threat. Static certificates used to authenticate devices to a network are issued once and then left on the machine like a sitting duck for months or years. Attackers are well aware of this vulnerability; as technology advances, cybercriminals continue to refine their tactics, making it crucial for cybersecurity solutions to evolve in tandem.
Dynamic Machine Authentication
QWERX's innovative approach to dynamic machine authentication provides a robust defense against credential harvesting. Unlike traditional static authentication methods, QWERX's Enterprise Security Perimeter (QESP) solution adapts to the dynamic nature of cyber threats, enhancing security measures and minimizing the risk of unauthorized access.
Key Features:
-
Ephemeral Keys: QESP eliminates static digital credentials (certificates and keys), which are the routine entry point for unauthorized network access. Instead of using static credentials to authenticate, this technology utilizes dynamic, ephemeral keys, which are generated locally and disappear immediately after authentication. There are no credentials stored to be stolen or misused.
-
Continuous Verification: QESP enforces continuous verification of every single device on a network. Zero Trust? The QWERX approach "mistrusts" all devices, all the time until they are authenticated. The verification process cycles repeatedly without end.
-
Real-Time Monitoring and Response: QESP provides real-time monitoring of attack attempts, allowing for immediate response to suspicious behavior. This proactive stance ensures that potential threats are rejected before they can even begin.
Conclusion
As credential harvesting continues to be a prominent threat in the digital landscape, the need for advanced and adaptive security solutions is more crucial than ever. QWERX's dynamic machine authentication solution stands out as a beacon of innovation, providing a robust defense against credential harvesting and bolstering the security defenses of enterprise organizations. With its' patented Ephemeral Key Infrastructure technology, QWERX sets a new standard for dynamic and proactive cybersecurity measures in the permanent struggle against cyber threats.