Secure DevOps
QWERX secures your development environment from Step Zero
250,000
average number of machine identities used by a single organization in 2021, expected to double by 2024
36%
of organizations surveyed by Ponemon in 2022 that say they have an inventory of every certificate and key within the organization
87%
of organizations surveyed by CyberArk reporting that secrets are stored in multiple places across DevOps environments
How many machines have access to your development environment?
Even one that you’re not tracking is one too many. DevOps teams require a diverse range of machines to connect, including hybrid IT environments that encompass public cloud instances, applications and services made up of microservices, containers, and APIs. To an attacker, each of these represents an entry point to your environment.
Step Zero: Secure the Environment
Before you can incorporate security into the applications and systems your team will design, you must ensure that the development environment is secure. The Step Zero assessment should include a plan for how all user and machine identities that will need access to the development environments will be tracked and managed. The DevSecOps team must have a high level of confidence that:
- The development environments are secured before any work begins
- The secure environments will be continuously maintained throughout the entire development lifecycle







SECURE
QWERX Automates DevOps Security
Our patented technology puts the security of your development environment on autopilot.
- Continuously authenticate all devices, multiple times per minute
- Block unauthorized devices that attempt to access the environment
- Manage and control all enrolled devices in a web-based console
QWERX Enterprise Security Perimeter (QESP) is a cloud-native SaaS that prevents unauthorized devices from accessing a protected network by replacing vulnerable static credentials with ephemeral rotating symmetric keys.
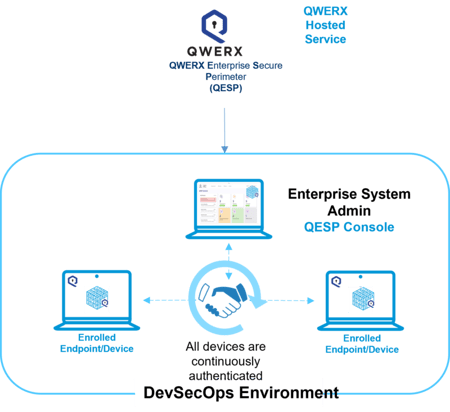
Here’s how it works. A common information source containing random, chaotic data is loaded into all networked devices. The QESP console initiates a “handshake” by sending instructions for building the initial key to all devices. Devices dynamically generate ephemeral keys to verify (or reject) a match, then the keys disappear and are never used again.
All devices across the network engage in continuous, orchestrated authentication. No keys are ever exchanged or stored – only instructions are exchanged in the clear to generate keys on each end.
The software seamlessly integrates into all existing networks and operating systems. Once networked devices and cloud instances are securely enrolled, all unauthorized authentication attempts are rejected and flagged. Real-time attack warnings are pushed to admins including metadata and telemetry.
QESP is built to scale to millions of endpoints and appliances within any Enterprise and has been analyzed by a U.S. Government Lab to be Quantum-Proof.
SPEED UP
No More Certificate Management =
Faster Development Cycles
Certificate management processes and approval workflows are an integral part of the software development lifecycle. Until now.
QWERX delivers a better way to secure the development environment without using static credentials, including certificates and keys. DevSecOps teams can get leaner and faster by eliminating:
- Time and money spent on certificate management
- Network downtime from expired certificates and other certificate lifecycle management issues
- Risk from misconfigured, misused, and/or unprotected TLS and code signing certificates
SIMPLIFY
Straightforward Security for DevSecOps
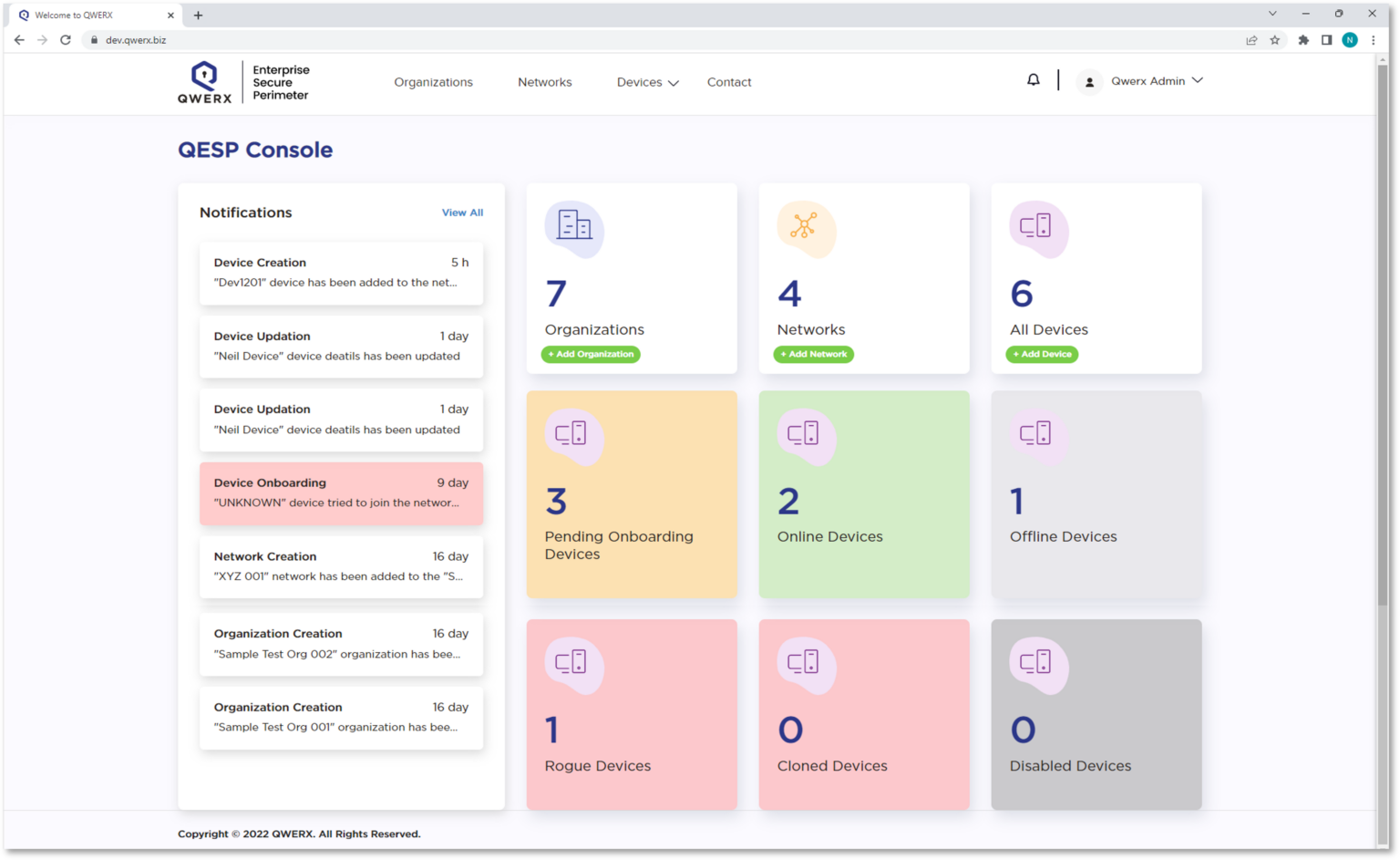
QWERX Enterprise Security Perimeter (QESP) can run on any network or operating system and prevents unauthorized devices from accessing protected networks. The QESP Console is designed to simplify machine identity management. Features include:
- A complete listing of all devices and endpoints across the protected network(s)
- Easy, one-time enrollment process for all devices that require access
- Ability to create as many networks as needed
- At-a-glance monitoring and real-time threat notifications
- Manage access of individual devices directly from console