Products
How it works
With QWERX, all endpoints on your network must continuously prove they belong.
Instead of taking the old trust but verify approach, a QWERX network practices zero trust + constant verification.
QESP is built on a patented and tested protocol which eliminates the use of digital certificates and private keys completely. It’s not just a patch for PKI; it’s a radical overhaul of secure network authentication.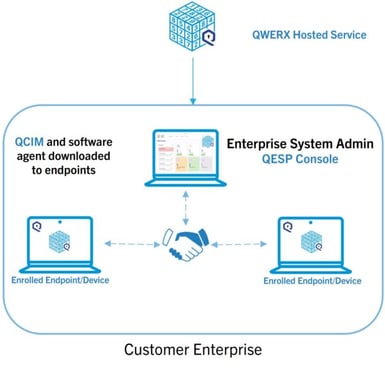
Here’s how it works:
- A common information source containing random, chaotic data is loaded into all networked devices
- The QWERX console initiates a handshake by sending instructions for building an initial key to all devices
- Devices dynamically generate ephemeral keys to verify (or reject) a match, then keys disappear
- All devices across the network engage in continuous, orchestrated authentication
A Unique Solution for a Common Problem
QESP was designed by technologists with deep expertise in information science, fraud detection, cryptography and identity management. The team leveraged their understanding of best practices in these fields (including symmetric key cryptography, zero trust, and continuous verification) into an enterprise software solution that improves the current state of network security by an order of magnitude.
The QWERX Chaotic Information Matrix (QCIM)
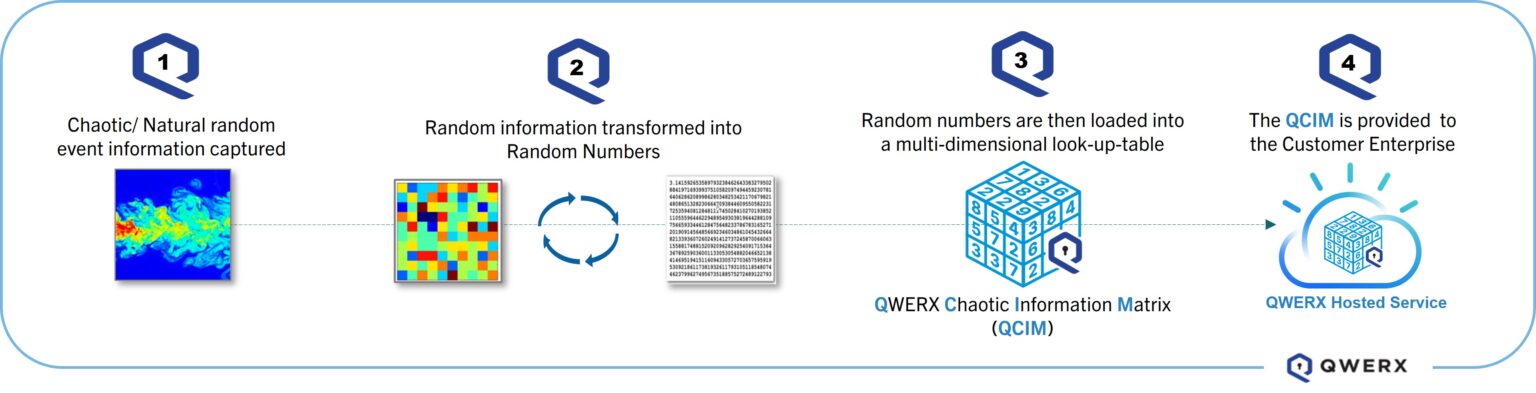
Unlike algorithmic data, chaotic information can’t be predictable by humans or advanced technology. That means it is inherently more secure than any algorithm-based solution.
QWERX patented a way to capture and transform nature’s chaotic events into pure, random information. This information is loaded into a multi-dimensional database that leverages common OLAP data structure.
We call this the QWERX Chaotic Information Matrix, or QCIM.
The QCIM is made available to the customer enterprise as part of the QWERX solution. Each enrolled device within the network is provisioned with a QCIM which is loaded with the initial set of random numbers. Learn more about quantum-resistant vs. quantum-proof cryptography.
Keys that aren’t stored can’t be stolen
 The QWERX console initiates a bi-directional “handshake” request to all enrolled devices. This request includes information about the location of the data to extract to build the initial authentication key.
The QWERX console initiates a bi-directional “handshake” request to all enrolled devices. This request includes information about the location of the data to extract to build the initial authentication key.
Each device decrypts the instructions and builds a temporary key. The keys are symmetric, meaning that all devices must come up with an exact match in order to authenticate to the network.
Keys are never exchanged or stored. Only instructions are exchanged, in the clear, to generate keys on each end.
Once a key is used for authentication, it disappears and is never used again. Learn more about how ephemeral keys solve a critical vulnerability of Public Key Infrastructure.
Each device is authenticated every few seconds

The QCIMs embedded in each enrolled device across the enterprise engage in continuous, orchestrated authentication.
The process of sending instructions, generating ephemeral keys, and authenticating or rejecting the device is repeated on a constant loop, eliminating any possibility for a digital credential to be stolen or copied and used to access the network.
Learn more about ephemeral rotation and how QWERX is using it to revolutionize cybersecurity.
Simplify Machine Identity Management
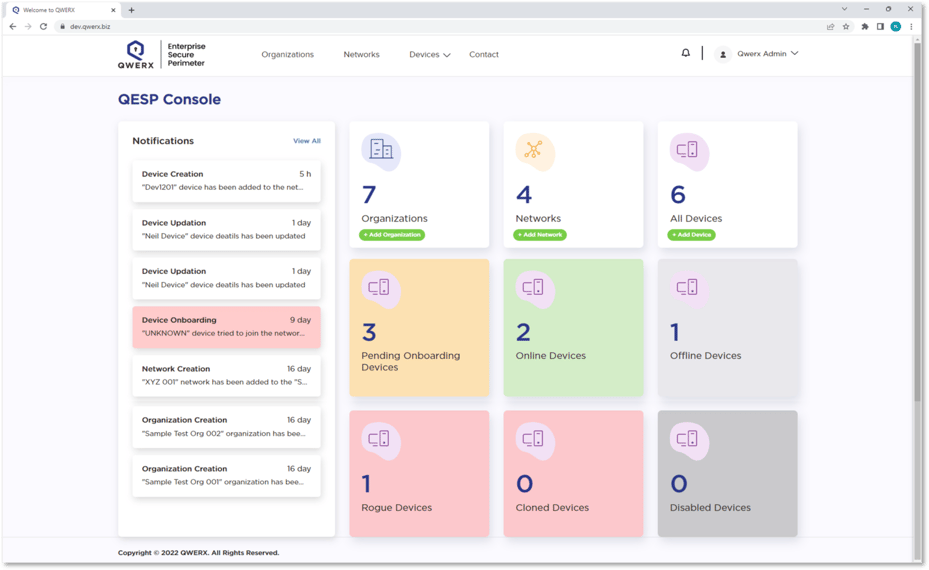
QWERX’s QESP Console is a simple and intuitive dashboard for viewing and managing all protected endpoints and networks.
- Manage QCIMs on all enrolled devices from a single pane of glass
- Automate continuous verification of all networked devices
- Receive real-time attack warnings, attack metadata and threat intelligence
- Detect, contain and restore rogue/clone devices
- Access reporting, analytics and audit trailing
- Scalable with no added complexity as machine identities rapidly increase
- Accessible via internet browser 24/7
...and say goodbye to Certificate Management
Part of what makes QESP so powerful is what it doesn’t do: store digital credentials, like keys and certificates. Since there is nothing to store, there is nothing to steal — or manage. QESP not only eliminates 80% of external attacks, it also eliminates all certificate lifecycle-related network outages. Your IT security team is free to pivot all the resources dedicated to certificate management to more mission-critical efforts.
QESP Technology Features
QESP is easy to install, easy to maintain, and easy to operate. Our software will run on any existing hardware, cloud, or operating system.
- Opensource foundations: developed from proven tech that scales to millions of endpoints without added complexity
- Cloud native: Docker container, device agnostic, multi-cloud and hybrid cloud deployment models supported
- Lightweight, extensible design: Python code base, RESTful APIs, JSON file exchange, MQTT protocol
- Lightweight management console runs in Cloud or on a Linux Server
- Operating system agnostic: MacOS, Windows and Linux supported
- Network agnostic: secure device handshakes at the Transport layer over existing insecure networks
- Easily layers and/or integrates with existing infrastructure
- Simple, plug-and-play SaaS implementation and management by Network Administrators; no end-user involvement
- Cost effective: no hardware requirements or associated costs
- Flexible subscription model, standard and custom payment methods available
An Ounce of Prevention…
is worth a pound of cure. And in today’s environment, taking a proactive stance now is worth so much more than the cost of curing the repercussions of your next cyberattack. QWERX designed QESP to protect your network against the types of external cyber breaches we understand today, as well as prevent future attacks that will be perpetrated with the help of evolving technology, including quantum computers.
Quantum-Proof
QESP harnesses pure, random chaotic data from nature that can never be predicted by technology
Secures IoT
Lightweight footprint with low processing requirement that can operate on IoT devices; no algorithms to create latency
Zero Trust
QESP advances your digital transformation efforts, strengthening your network with continuous verification
Download the QESP Data Sheet 
Download our two-page data sheet to learn more about QWERX’s innovative technology. QESP is a lightweight, software-only solution that installs directly on network devices and is managed from a central browser-friendly console. It is not disruptive to existing infrastructure and plays well with others.


