Is Your Cybersecurity Cloud Computing Really That Secure?

Cybersecurity in cloud computing poses a significant challenge to organizations and their employees. Indeed, 79% of companies have experienced at least one cloud data breach, according to the State of Cloud Security Maturity 2022. Stolen credentials or malware-infected devices could shut down your network and wreak havoc on operations.
Secure cloud computing requires a multilayered approach. It should reduce the human risk factor, monitor user and device access and collect data. Learn about the pitfalls of cloud computing and how you can overcome them to harden your system.
Flawed Identity and Access Management Processes
Many businesses shifted to cloud computing out of necessity, only to realize their existing cybersecurity measures were ill-prepared for cloud hazards. To address these concerns, companies put together piecemeal solutions, using different tools for employee logins, device registration and network protection.
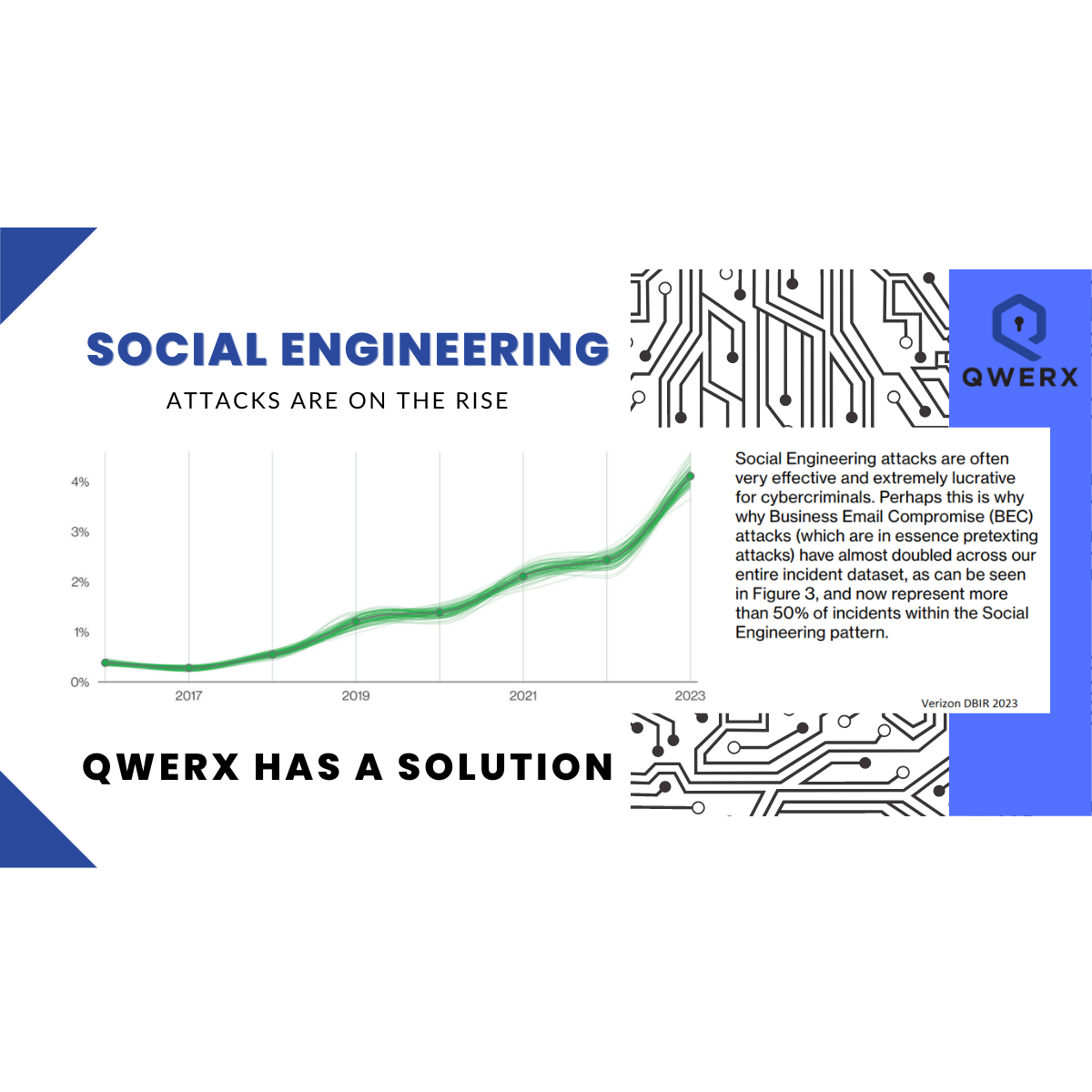
Yet, the Cloud Security Alliance (CSA) found that "insufficient identity, credentials, access and key management" is the number one risk of cloud computing in 2022, whereas it was number four in 2019. This problem is compounded by the fact that more than 20% of companies worldwide have over "1,500 account passwords that don't expire."
Solutions like public key infrastructure (PKI) are safer than traditional passwords, but 56% of Ponemon survey respondents say "encryption key management is painful." Businesses need a simple tool that is easy to install and use. It should eliminate user error and use rotating symmetric keys, which harden your network against future quantum attacks.
Insufficient Cloud Security Architecture
Cloud security architecture refers to technologies and hardware that protect the cloud's workloads, systems and data. Modern cloud environments can become fragmented and complex, increasing the probability of errors and access control issues. Consequently, CSA identified a lack of security planning and architecture as a core cybersecurity cloud computing issue.
QWERX fits seamlessly into your security strategy, creating a zero-trust network. It authenticates devices multiple times per second using ephemeral keys and chaotic information. Best of all, QWERX is device, operating system and network agnostic, making it easy to integrate with your tech stack.
Higher Costs Associated With Cybersecurity for Cloud Computing
Deploying multiple cloud security solutions is expensive, considering you must secure every network application, device and user identity. However, a data breach can wipe out your annual budget within days or weeks. IBM reported that a data breach's average cost was $4.35 million in 2022, an increase of 12.7% since 2020. And over 80% of surveyed companies had more than one data breach.
IBM also noted that "45% of the breaches were cloud-based," and "60% of organizations' breaches led to increases in prices passed on to customers." Adopting a zero trust solution that is centrally managed is the most cost-effective way to protect your business. QWERX works by monitoring access attempts in real time, shutting down rogue devices and sending an alert before damage occurs.
Complicates Compliance and Auditing Management
Compliance and auditing are the most common challenges when using cloud-based infrastructure as a service (IaaS). This is due, in part, to problems with access. According to a SailPoint report, nearly one-third of businesses reported that the wrong individuals have privileged access and a quarter of companies said they have unauthorized users.
QWERX Enterprise Secure Perimeter (QESP) incorporates policy management at several levels, thanks to our team's ample experience in regulatory and technology policies. It continually authorizes devices, not credentials entered by humans. As a result, your staff can spend less time monitoring compliance and auditing requirements and more time on mission-critical activities.
Enable Secure Cloud Computing With QWERX
The benefits of cloud technologies are immense, as are the threats to your organization. A secure cloud computing solution hardens your network today and scales as your perimeter increases. Eliminate cybersecurity risks in cloud computing with an easy-to-deploy, quantum-proof solution. Contact us to learn how QWERX helps you overcome the challenges of cloud environments.
Jessica Elliott is a business technology writer specializing in cloud services and cybersecurity. Her work appears in U.S. News, Business.com and Investopedia.
Sources
Ermetic - State of Cloud Security Maturity 2022
Cloud Security Alliance - Cloud Security Alliance’s Top Threats to Cloud Computing
Varonis - 2021 Data Risk Report
Ponemon Institute - 2021 Global Encryption Trends Study
IBM - Cost of a Data Breach Report 2022
SailPoint - State of IaaS Cloud Infrastructure Security and Governance