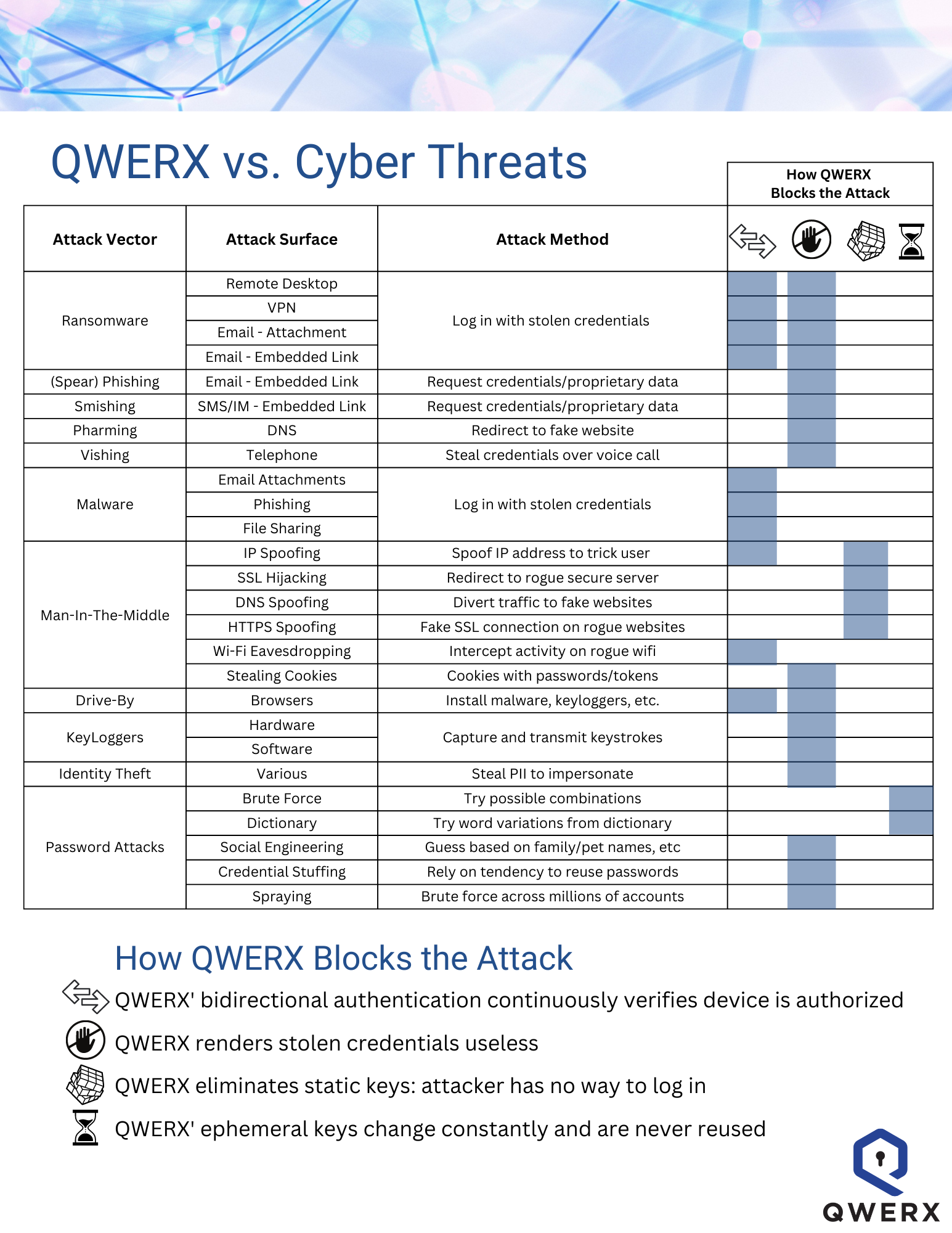
QWERX vs. Cyber Threats
The cybersecurity space is crowded with vendors who make big claims about their solutions. "What" the products deliver are generally the same -- improve an organization's security posture, minimize vulnerability to cyber threats. But what is most interesting to us (and more complicated to communicate), is "how" this result is accomplished. QWERX' patented technology delivers the desired result: elimination of significant percentage of attack surface, elevated network security, fewer cyberattacks. In the chart below, we break down how the software prevents different types of common cyber threats.
Bidirectional Authentication Continuously Verifies Device is Authorized
QWERX software automates continuous verification of all enrolled devices across a protected network. Each device generates a new authentication key every few seconds, which must match the key that is generated on all other devices. No match? No access. This orchestrated handshake is repeated on a continuous loop, each time with a fresh authentication key that is never re-used.
QWERX' bidirectional authentication blocks all cyberattacks that attempt to use stolen credentials to gain access to a protected network from an unenrolled device. These attack types include Ransomware, Malware, IP Spoofing, Wi-Fi Eavesdropping, and Drive-by Downloads. The automated frequency of authentication makes it impossible for an unenrolled device to get in, regardless of the credentials.
Stolen Credentials are Rendered Useless
Within a security infrastructure, there are two types of identities that must be verified: User Identity (human) and Machine Identity (device).
User Identity is most commonly verified with a password. Password breaches are becoming increasingly common. Cyber hygiene is important, but until there is a perfect solution for authenticating a user's identity, we should assume that passwords can and will be stolen. Types of cyberattacks that use a stolen password to access a system or network include KeyLoggers which capture and transmit keystrokes, certain types of Phishing that involves tricking a user into providing their passwords or other private data, Identity Theft, Social Engineering, Credential Stuffing, and Spraying.
Machine Identity is verified in today's security infrastructure with static digital credentials and keys, which are stored locally in the device. Attackers may employ various methods to steal or duplicate these digital credentials and attempt to use them to access a desired network.
QWERX blocks all cyberattacks that attempt to use a stolen password, digital credential or key to gain access to a protected network from an unenrolled device. Our patented ephemeral key infrastructure (more on this below) makes it impossible to use stolen credentials of an enrolled device, and the automated frequency of authentication makes it completely impossible for an unenrolled device to get in, regardless of the credentials used.
No Static Keys = No Way for Attacker to Log In
Cyberattacks that operate by intercepting communication between two parties are called Man-in-the-Middle attacks. The attacker may use a fake wireless access point or other method of gaining access to a network. Once the attacker has inserted themselves between the two parties, they can then manipulate the data being sent or received, allowing them to steal confidential information, gather technology-related intelligence, impersonate one of the parties, or gain access to sensitive systems.
QWERX prevents Man-in-the-Middle attacks before they can happen, by employing ephemeral key infrastructure, in which cryptographic keys persist for a matter of seconds or even fractions of a second, thereby eliminating the possibility for an attacker to gain access to a protected network from an unenrolled device in the first place.
Ephemeral Keys Change Constantly and are Never Reused
In cyberattacks like Brute Force and Dictionary attacks where the attacker attempts to guess a static password, time is on their side. The more time they have to guess, the more likely they will come up with the right answer, and advanced computing could increase the speed of guessing exponentially. The average certificate lifecycle runs 13 months, with some certificates lasting for twenty years before expiring. Best practices dictate that passwords should be changed every 60 to 90 days, or possibly less frequently.
QWERX' ephemeral key infrastructure radically changes that calculation. With this technology, a new key may be dynamically generated every few seconds, used to authenticate the device, and is then erased, never to be used again. Even if it was somehow possible for a quantum computer to guess correctly, the authentication key is set to rotate a few seconds later. For the first time ever, time becomes a weapon that enterprises can use against attackers.
QWERX Blocks Cyberattacks
In today’s digital world, organizations must be prepared to defend against cyber threats. QWERX' patented cybersecurity technology eliminates cyber threats in a new way that is both more sophisticated and easier to implement. Our cloud-native software enhances the security team's capabilities by providing a comprehensive listing of all enrolled machines on their network and delivering timely threat intelligence. Not only does QWERX help protect organizations against cyber threats, but it also helps organizations stay compliant with industry regulations, protect their data, and maintain a secure environment.
Today's corporations and specifically their security professionals, are always under scrutiny and there is an enormous amount of pressure from customers and shareholders to protect their assets and intellectual property. QWERX helps organizations stay one step ahead of cyber threats and protect their assets from malicious actors.